Tabnabbing is computer exploits and phishing attack, which persuades users to submit their login details and passwords to popular websites by impersonating those sites and convincing the user that the site is genuine. The attack's name was coined in early 2010 by Aza Raskin, a security researcher and design expert. The attack takes advantage of user trust and inattention to detail in regard to tabs, and the ability of modern web pages to rewrite tabs and their contents a long time after the page is loaded. Tabnabbing operates in reverse of most phishing attacks in that it doesn�t ask users to click on an obfuscated link but instead loads a fake page in one of the open tabs in your browser. Source Wikipedia.
The Tabnabbing attack method is used when a victim has multiple tabs open, when the user clicks the link, the victim will be presented with a �Please wait while the page loads�.
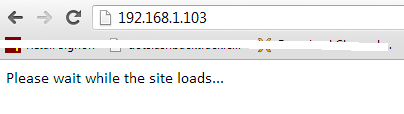
In this attack, the main aim of the attacker is to redirect the browser to its fake login page where the victim can input his/her credentials.
How it is done:
Step 1: Load your Backtrack machine and the open the terminal and
Type: cd /pentest/exploits/set/ HIT ENTER
Step 2. type: ./set HIT ENTER
This will open Social Engineering toolkit. The Social-Engineer Toolkit (SET) was created and written by the founder of TrustedSec. It is an open-source Python-driven tool aimed at penetration testing around Social-Engineering. SET has been presented at large-scale conferences including Blackhat, DerbyCon, Defcon, and ShmooCon. With over two million downloads, SET is the standard for social-engineering penetration tests and supported heavily within the security community.
The Social-Engineer Toolkit has over 2 million downloads and is aimed at leveraging advanced technological attacks in a social-engineering type environment. TrustedSec believes that social-engineering is one of the hardest attacks to protect against and now one of the most prevalent. The toolkit has been featured in a number of books including the number one best seller in security books for 9 months since its release,�Metasploit: The Penetrations Testers Guide�written by TrustedSec�s founder as well as Devon Kearns, Jim O�Gorman, and Mati Aharoni.
You can also download Social Engineering Toolkit for Windows.
Step 3. Now type: 1 and HIT ENTER which is social engineering.
Step 4.> Now type: 2 and HIT ENTER which is website attack vendors
Step 5.> type 4 and HIT ENTER which is tabnabbing attack method.
Step 6.> type: 2 and HIT ENTER which is site cloner.
Enter your IP and HIT ENTER and also type the url you want to clone.In this I am cloning gmail.com and hit enter and again hit enter.
You can see now the tabnabbing attack is enabled now.
So now the last step is to open your browser and type the IP address which was set by you in the url bar and HIT ENTER.
This will redirect to the fake page which has been cloned. Whenever the victim types the username and password in it, it automatically redirects and the credentials will get to us.
Enjoy!!!!











No comments:
Post a Comment